HIPAA Compliance Services
HIPAA COMPLIANCE SERVICES
HIPAA COMPLIANCE SERVICES
HIPAA Compliance Services utilizing the Six Sigma DMAIC process to achieve and maintain HIPAA compliance for our clients.
Our collaborative strategy is a data-driven process. We help our clients to maintain reasonable and appropriate administrative, technical, and physical safeguards for protecting e-PHI.
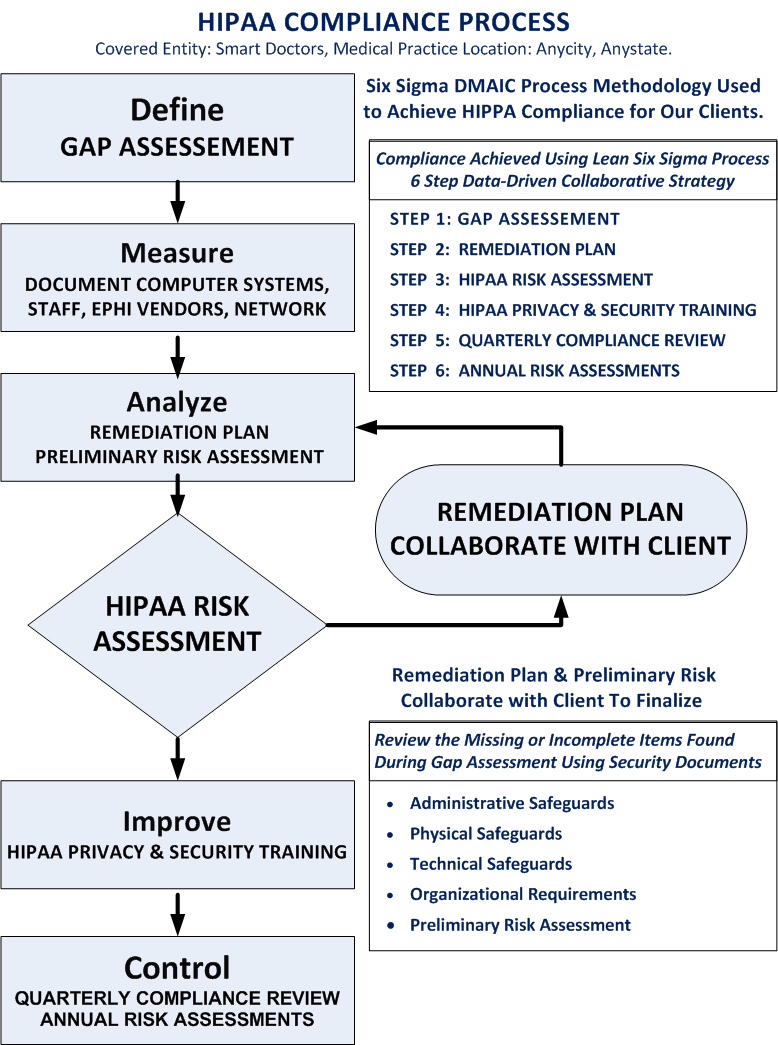
DMAIC is an acronym that stands for Define, Measure, Analyze, Improve, and Control.
The Security Rule establishes a set of national standards for confidentiality, integrity and availability of e-PHI.
The Security Rule requires covered entities to maintain reasonable and appropriate administrative, technical, and physical safeguards for protecting e-PHI.
Specifically, covered entities must:
Ensure the confidentiality, integrity, and availability of all e-PHI they create, receive, maintain or transmit;
Identify and protect against reasonably anticipated threats to the security or integrity of the information;
Protect against reasonably anticipated, impermissible uses or disclosures; and
Ensure compliance by their workforce
Gap Assessment The Defining Phase
Client Interview Process
Interview covered entity's staff to understand the client's current use of their information systems.
Document client's requirements and business critical applications.
Define ePHI vendors, cloud service providers, and business partners.
Onsite Review of Information Systems
Inventory of all information systems hardware and software.
Physical networking topology reviewed.
Cyber Security Vulnerability Review
Network vulnerability scanning, port scanning with active reconnaissance.
Complete hardware and software profiles of all workstation and servers.
Security and compliance scanning of all workstations and servers.
Embedded systems reviewed for known vulnerabilities, outdated firmware, default configurations, and insecure configuration settings.
Remediation Plan & Risk AssessmentThe Measuring & Analyzing Phase
Gap Assessment Collaborative Review
Review the missing or incomplete items found during the Gap Assessment with our clients to develop a roadmap to achieve HIPAA compliance.
Risk Analysis and Management
The Administrative Safeguards provisions in the Security Rule require covered entities to perform risk analysis as part of their security management processes.
Results produce the Risk Assessment documentation and the Remediation Plan documentation.
Define Policies and Procedures
A covered entity must adopt reasonable and appropriate policies and procedures to comply with the provisions of the Security Rule. A covered entity must maintain, until six years after the later of the date of their creation or last effective date, written security policies and procedures and written records of required actions, activities or assessments.
Maintain Compliance & Staff TrainingThe Improving & Controlling Phase
Implement The Remediation Plan
The Remediation Plan is a road map to achieving HIPAA compliancy.
Quarterly Reviews
Perform quarterly reviews of covered entity information systems.
Implement the Remediation Plan based on documented target dates..
The Administrative Safeguards provisions in the Security Rule require covered entities to perform risk analysis as part of their security management processes.
Security Awareness Training
The Administrative Safeguards provisions in the Security Rule require covered entities to implement a security awareness and training program for all members of the workforce (including management).
Yearly Risk Analysis
Risk analysis should be an ongoing process, in which a covered entity regularly reviews its records to track access to e-PHI and detect security incidents, periodically evaluates the effectiveness of security measures put in place, and regularly reevaluates potential risks to e-PHI.
Interested in our services? We’re here to help!
We want to know your needs exactly so that we can provide the perfect solution. Let us know what you want and we’ll do our best to help.